Combinatorial Security Testing for Bluetooth Low Energy accepted at USENIX ATC
Bluetooth Low Energy is one of the most widely used protocols used in Internet of Things (IoT) and multimedia devices. Security issues in these applications are prone to affect a significant number of end users and companies alike.
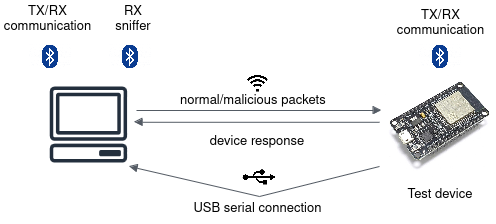
In their latest work applying the Combinatorial Security Testing (CST) approach to Bluetooth Low Energy devices, Dominik Schreiber, Manuel Leithner, Jovan Zivanovic and Dimitris Simos of the MATRIS group of SBA Research, the researchers uncovered 19 distinct vulnerabilities in 10 Bluetooth LE devices. Most of these issues could be used to remotely freeze the devices indefinitely (also known as a Denial of Service), while others lead to incorrect behavior or core dumps being emitted over debugging connections, indicating potentially exploitable conditions. The work is originally based on a fuzzing approach called SweynTooth but extended towards combinatorial security testing, offering a mathematically guaranteed degree of coverage based on an attack grammar.
Setup
All affected vendors were contacted to facilitate a coordinated responsible disclosure process, minimizing the impact to end users by enabling device manufacturers to release updated firmware versions before vulnerabilities are published. Additionally, related CVEs are in the process of being assigned.
The work titled Bluetooth Low Energy Security Testing with Combinatorial Methods has been accepted to the 2025 USENIX Annual Technical Conference and will be presented in July 2025 in Boston, MA.