Decision Framework Model for Cloud Based System Migration
The increasing distribution of cloud services comes with significant benefits but also substantial risks to privacy and security. The goal of this project was to develop a decision framework model regarding the adaption of and the migration to cloud-based systems into existing infrastructure.
Project Outline & Findings
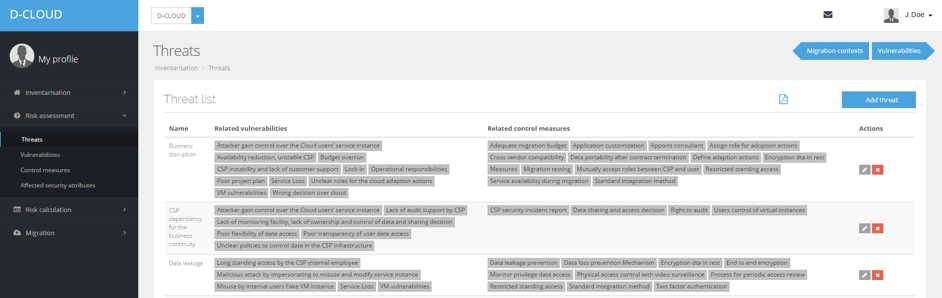
We created a taxonomy of social engineering attacks to classify attacks. Social Engineering is one the most important attack vectors against “knowledge workers”. Moreover, it is important to understand how social engineering attack scenarios differ when system infrastructure components are migrated into the cloud. In addition, we looked at important components such as the network work infrastructure to build components of the decision framework and a process for migration and autonomic management. We then extended extends the state of the art by providing insights into the migration needs and risks that that hinder cloud migration in a corporate environment.
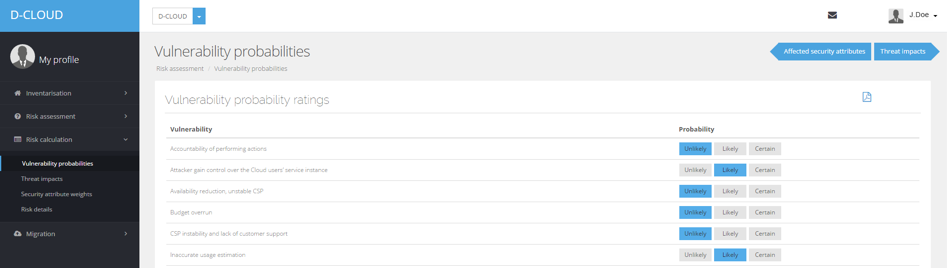
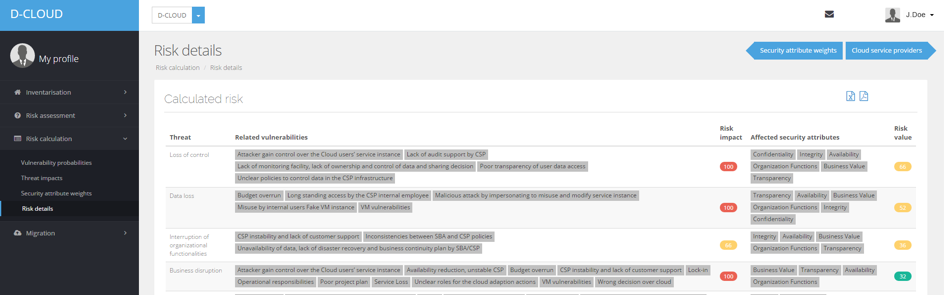
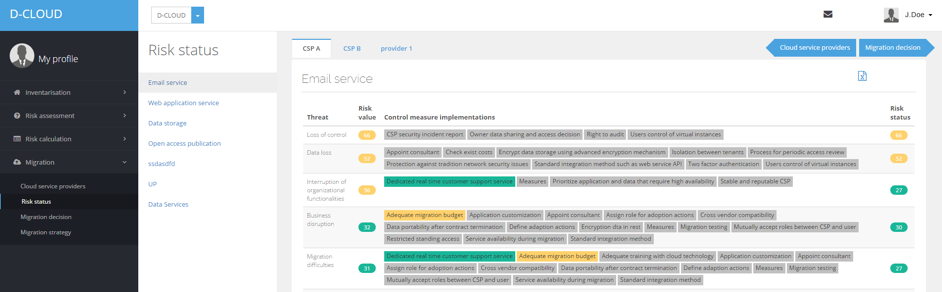
Based on these finding we developed a software prototype to support an effective, fast and well-informed decision based on the risks of a migration to the cloud. The tool also estimates risks and determines cost associated with specific requirements.
We finally evaluated both the theoretical framework and the prototype implementation in two real-world use cases industrial contexts by applying both Theo case study research method and action research.
Publications
- Krombholz, Katharina, Heidelinde Hobel, Markus Huber, and Edgar Weippl. “Social engineering attacks on the knowledge worker.” In Proceedings of the 6th International Conference on Security of Information and Networks, pp. 28-35. ACM, 2013. (Green OA)
DOI 10.1145/2523514.2523596
PDF - Krombholz, Katharina, Heidelinde Hobel, Markus Huber, and Edgar Weippl. “Advanced social engineering attacks.” In Journal of Information Security and applications 22 (2015): pp.113-122. (Green OA)
DOI 10.1016/j.jisa.2014.09.005
PDF - Ullrich, Johanna, Katharina Krombholz, Heidelinde Hobel, Adrian Dabrowski, and Edgar R. Weippl. “IPv6 Security: Attacks and Countermeasures in a Nutshell.” In WOOT. 2014.
PDF
PDF - Ismail, Umar Mukhtar, Shareeful Islam, Moussa Ouedraogo, and Edgar Weippl. “A Framework for Security Transparency in Cloud Computing.” In Future Internet 8, no. 1 (2016): 5 (Gold OA)
DOI 10.3390/fi8010005
PDF - Islam, Shareeful, Moussa Ouedraogo, Christos Kalloniatis, Haralambos Mouratidis, and Stefanos Gritzalis. “Assurance of Security and Privacy Requirements for Cloud Deployment Model.” IEEE Transactions on Cloud Computing (2015). (Green OA)
DOI 10.1109/TCC.2015.2511719
PDF - Rahman, Alifah Aida Lope Abdul, and Shareeful Islam. “Sustainability forecast for cloud migration.” In Maintenance and Evolution of Service-Oriented and Cloud-Based Environments (MESOCA), 2015 IEEE 9th International Symposium on the, pp. 31-35. IEEE, 2015. (Green OA)
DOI 10.1109/MESOCA.2015.7328123
PDF - Islam, Shareeful, Edgar R. Weippl, and Katharina Krombholz. “A decision framework model for migration into cloud: Business, application, security and privacy perspectives.” In Proceedings of the 16th International Conference on Information Integration and Web-based Applications & Services, pp. 185-189. ACM, 2014. (Green OA)
10.1145/2684200.2684354
PDF - Islam, Shareeful, Haralambos Mouratidis, and Edgar R. Weippl. “An empirical study on the implementation and evaluation of a goal-driven software development risk management model.” In Information and Software Technology 56, no. 2 (2014): pp. 117-133. (Green OA)
10.1016/j.infsof.2013.06.003
PDF
Further Information
- This project was led by SBA Research.
- Download Abstract
- Download Final Report Abstract
Contact
This project was funded by the Austrian Science Fund (FWF) P 26289-N23.